For this installment in my series about FTP Clients I'm going to review the FTP features in Microsoft's Expression Web 4 (EW4). You can find out more about the Microsoft Expression series of products from the following URL:
http://www.microsoft.com/expression/
Note: There are a lot of really cool features that are built into EW4, like Search Engine Optimization (SEO) tools, rich extensibility APIs, previewing content side-by-side in multiple browser windows through SuperPreview, built-in support for programming languages like ASP/ASP.NET/PHP/etc. But that being said, in keeping with the main theme of my FTP client series, this review is focusing on just the FTP aspects of EW4 - not the entire product.
 |
| EW4 Splash Screen |
At the time of this blog post, EW4 is a for-retail product that is available as part of the Expression Studio 4 Web Professional and Expression Studio 4 Ultimate suites.
Expression Web 4 Overview
The EW4 user interface follows the same design paradigm as earlier versions of Expression Web, albeit with the darker color scheme that Expression products have been using in recent versions. While EW4 contains many features that you would expect in a Microsoft Office application, it does not resemble the Office 2007/2010 user interface, so there is no ribbon-style toolbar. (This is a bad thing if you love the Office ribbon and a good thing if you hate the Office ribbon; but I'll leave that up to you to decide. <grin>)
 |
| Fig. 1 - EW4's built-in support for PHP Files |
One minor personal issue that I have with Expression Web is that VBA was deprecated a while ago, so EW4 doesn't have a macro language that I can use to automate tasks like I would do with previous versions. It's possible to create "add-ins" for Expression Web, but there's a lot of overhead associated with that. From my perspective, that's pretty much like saying to someone, "I know that you would like to get across town and you already have a really nice car, but we're going to take that away. If you take 17 different buses and then walk three or four blocks, you will eventually wind up where you want to go. Of course, it will take you several hours longer and it's a really big hassle, but sooner or later you'll get there." (No comments about carbon footprint - please. <grin>)
That being said, EW4 is a great web site editor and is a good FTP client, and EW4 is much better than its predecessors. (Note: By "predecessors" I mean earlier versions of Expression Web and FrontPage.) I'll explain more in the following sections of this post.
Opening an FTP Site
Opening a site is straight-forward, and for the most part the user interface is the same whether you are opening a site over FTP/FTPS or over HTTP using WebDAV or FPSE.
 |
| Fig. 2 - Opening a Site in EW4 |
When you are opening an FTP or HTTP site for the first time, your list of managed sites will be empty. As you open sites, the list of sites will be populated for each site there you have the Add to managed sites check box selected.
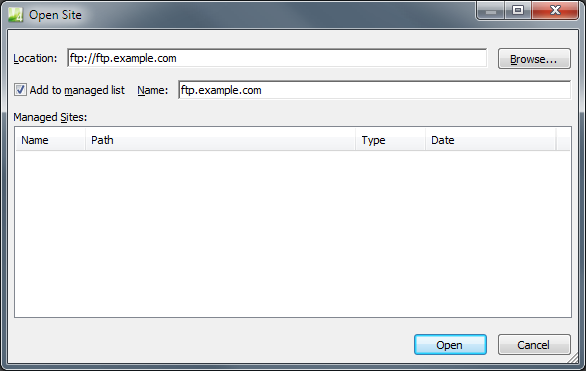 |
| Fig. 3 - EW4's Open Site Dialog Box |
Once you have entered your site information, EW4 will prompt you for your remote editing options. This allows you to choose between editing the live site over FTP or editing a local copy and publishing your changes at a later date & time.
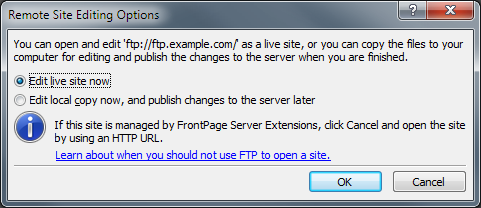 |
| Fig. 4 - EW4's Remote Site Editing Options Dialog Box |
The last dialog before opening the FTP site is the all-too-familiar prompt for your user credentials, albeit with a warning about FTP credentials being transmitted without encryption. (This is why you should use FTPS, but I'll discuss that later in this post.)
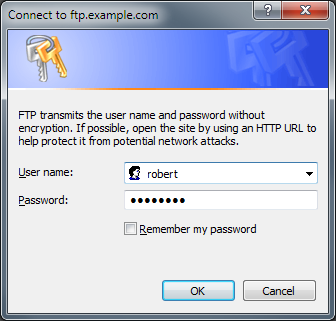 |
| Fig. 5 - EW4's Remote Site Editing Options |
Once the credentials have been verified by the FTP server, EW4 will display your site and you can begin editing your content.
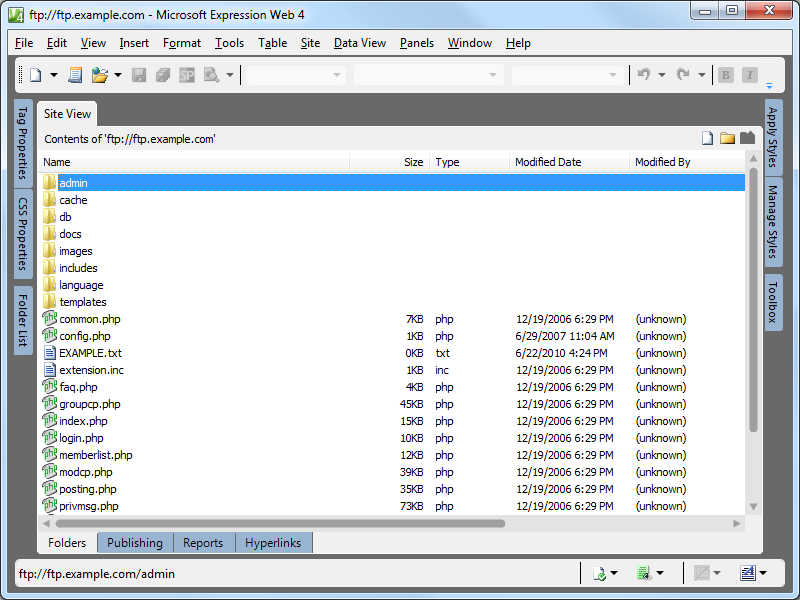 |
| Fig. 6 - An example phpBB site opened in EW4 |
EW4 has some basic site management functionality, which is accessed through the Site -> Manage Site List menu. From there you can add or remove sites from the list. Unfortunately you cannot modify the settings for sites in the list; you have to remove and re-add sites with different settings.
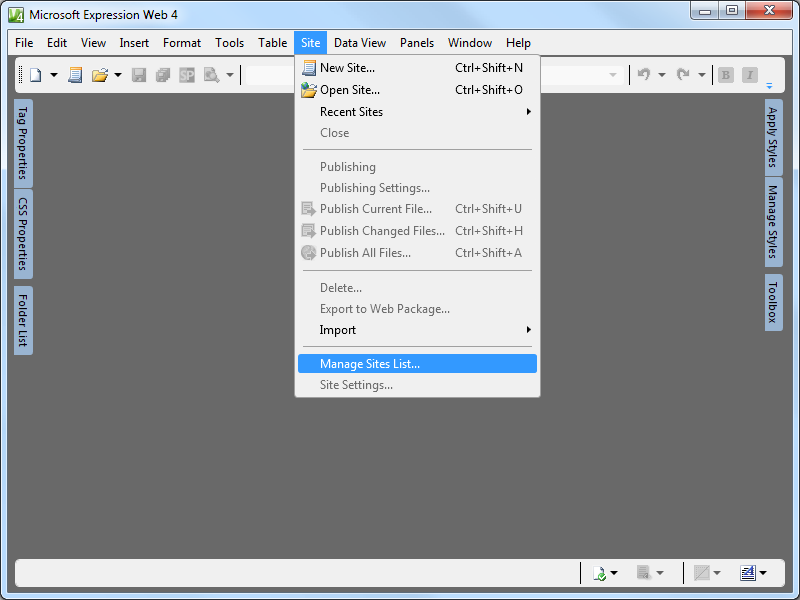 |
| Fig. 7 - Opening the EW4 Site Manager |
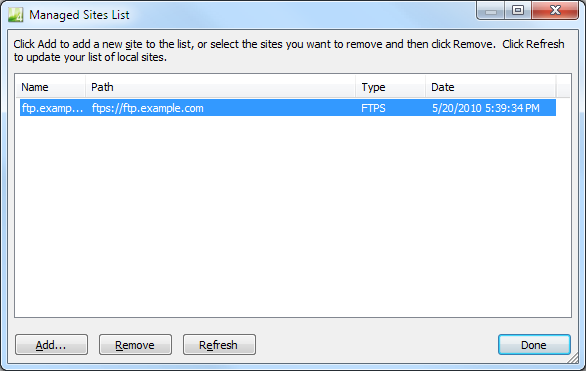 |
| Fig. 8 - Viewing the list of managed sites |
That's it for the simple stuff - now we'll take a look at the specific FTP topics that I've discussed in my other FTP client blog posts.
Using EW4 with FTP over SSL (FTPS)
EW4 supports both Implicit and Explicit FTPS, so the choice is up to you to decide which method to use. The FTPS method is specified by the port number that you choose when you are connecting.
I realize that I have posted the following information in almost all of my posts in this FTP client series, but in the interests of completeness it needs to be said again - the following rules apply for FTP7 when determining whether you are using Implicit or Explicit FTPS:
- If you enable SSL in FTP7 and you assign the FTP site to port 990, you are using Implicit FTPS.
- If you enable SSL in FTP7 and you assign the FTP site to any port other than port 990, you are using Explicit FTPS.
EW4 doesn't have a way of specifying Explicit or Implicit FTPS other than the port numbers listed above. That being said, more often than not you will probably be using Explicit FTPS on the default port (21) so you won't need to enter a port at all.
For example, if you are using EW4 with Explicit FTPS on the default port, you can skip adding a port number.
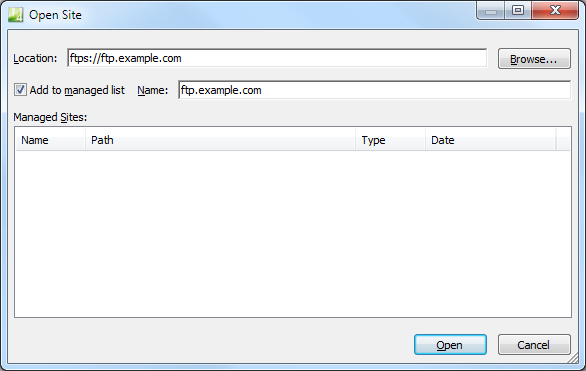 |
| Fig. 9 - Opening a site using Explicit FTPS |
However, if you are using Implicit FTPS, you need make sure that you configure EW4 to connect on port 990.
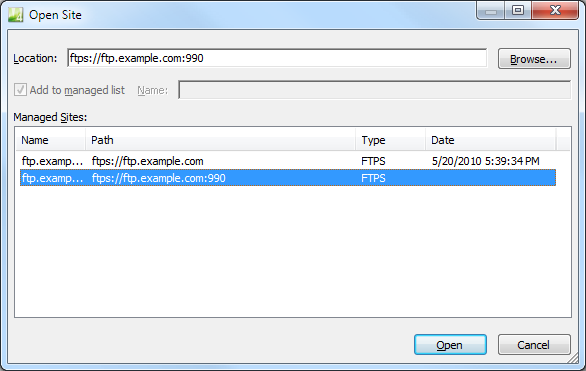 |
| Fig. 10 - Opening a site using Implicit FTPS |
Using EW4 with FTP Virtual Host Names
Because EW4's login dialog allows you to specify the virtual host name as part of the user credentials, EW4 works great with FTP7's virtual host names. All that you need to do is use the "ftp.example.com|username" or "ftp.example.com\username" syntax when specifying your username, and when you connect to the FTP7 server it will route your requests to the correct FTP virtual host site.
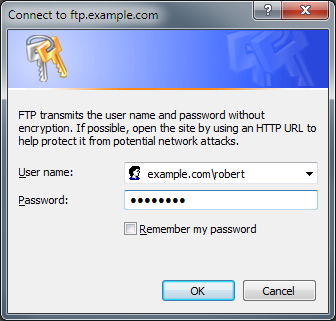 |
| Fig. 11 - Specifying an FTP Virtual Host name |
EW4 Does Not Support True FTP Hosts
Unfortunately EW4 does not have built-in for the HOST command, nor does it have support for entering commands that will be sent before the client has logged in, so you cannot use true FTP host names when using EW4 to connect to FTP7 sites that are configured with host names.
Scorecard for Expression Web 4
This concludes our quick look at some of the FTP features that are available with EW4, and here are the scorecard results:
Note: I've included the following disclaimer in all of my posts, and this post is no exception - there are a great number of additional features that EW4 provides - once again I'm just keeping the focus on those topic areas that apply to FTP7. ;-]
Note: This blog was originally posted at http://blogs.msdn.com/robert_mcmurray/